
Getty Images
How to set up a VLAN for enterprise networks
VLANs can secure and prioritize network traffic. To set up VLANs correctly, teams should understand concepts like VLAN tagging and subnets.
Virtual LANs, or VLANs, separate and prioritize traffic on network links. They create isolated subnets that enable certain devices to operate together, regardless of whether they're on the same physical LAN.
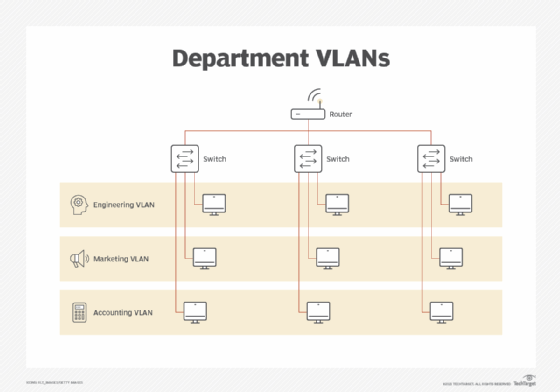
Enterprises use VLANs to partition and manage traffic. For example, a company looking to separate its engineering department's data traffic from the accounting department's traffic can create separate VLANs for each department. Multiple applications that execute on the same server can share a link, even if they have different requirements. A video or voice application with stringent throughput and latency requirements can share a link with an application with less critical performance requirements.
How do VLANs work?
Traffic on individual VLANs is delivered only to the applications assigned to each VLAN, providing a level of security. Each VLAN is a separate collision domain, and broadcasts are limited to a single VLAN. Blocking broadcasts from reaching applications connected to other VLANs eliminates the need for those applications to waste processing cycles on broadcasts not intended for them.
VLANs operate at Layer 2, the link layer, and can be limited to a single physical link or extended across multiple physical links by connecting to Layer 2 switches. Because each VLAN is a collision domain and Layer 3 switches terminate collision domains, VLAN segments can't be connected by a router. Essentially, a single VLAN can't span multiple subnets.
Subnet segments connect via switches. It's common to connect components of an application executing on multiple servers by placing them on a single VLAN and subnet. For example, a single subnet and VLAN may be dedicated to the accounting department, but if department members are too far apart for a single Ethernet cable, switches connect the different Ethernet links that carry the VLAN and subnet, while VLAN routers connect the subnet to the rest of the network.
VLAN trunk links carry more than one VLAN, so packets on a trunk carry additional information to identify its VLAN. Access links carry a single VLAN and don't include this information. Bits are removed from the packet connected to the access link, so a connected port receives just a standard Ethernet packet.
How to set up a VLAN
Setting up a VLAN can be complicated and time-consuming, but VLANs offer significant advantages to enterprise networks, such as improved security. The steps to set up a VLAN are as follows.
1. Configure the VLAN
All the switches that carry the VLAN must be configured for that VLAN. Whenever teams make changes to the network configuration, they must take care to update switch configurations, swap out a switch or add an additional VLAN.
2. Set up access control lists
ACLs, which regulate the access granted to each user connected to a network, also apply to VLANs. Specifically, VLAN ACLs (VACLs) control the access to a VLAN wherever it spans a switch or where packets enter or exit the VLAN. Network teams should pay close attention when configuring VACLs, as setting them up is often complicated. Network security can be compromised if an error occurs when VACLs are configured or modified.
3. Apply command-line interfaces
Each OS and switch vendor specifies a set of CLI commands to configure and modify VLANs on its product. Some administrators construct files containing these commands and edit them when necessary to modify the configuration. A single error in the command files can cause one or more applications to fail.
4. Consider management packages
Equipment vendors and third parties offer management software packages that automate and simplify the effort, reducing the chance of error. Because these packages often maintain a complete record of each set of configuration settings, they can quickly reinstall the last working configuration in the case of an error.
Identifying VLANs with tagging
The IEEE 802.1Q standard defines how to identify VLANs.
The destination and source media access control addresses appear at the beginning of Ethernet packets, and the 32-bit VLAN identifier field follows.
Tag protocol identifier
The TPID makes up the first 16 bits of the VLAN frame. The TPID contains the hexadecimal value 8100, which identifies the packet as a VLAN packet. Packets without VLAN data contain the EtherType field in the packet position.
Tag control information
The 16-bit TCI field follows the TPID. It contains the 3-bit priority code point (PCP) field, the single-bit drop eligible indicator (DEI) and the 12-bit VLAN identifier (VID) field.
The PCP field specifies the quality of service required by the applications sharing the VLAN. The IEEE 802.1p standard defines these levels as the following values:
- Value 0 indicates a packet that the network makes its best effort to deliver.
- Value 1 identifies a background packet.
- Value 2 through value 6 identify other packets, including values indicating video or voice packets.
- Value 7, the highest priority, is reserved for network control packets.
The single-bit DEI follows the PCP field, and it adds further information to the PCP field. The DEI field identifies a packet that can be dropped in a congested network.
The VID field consists of 12 bits that identify any of the 4,096 VLANs a network can support.
Ethernet-based VLANs
Ethernet-based VLANs can be extended to Wi-Fi using a VLAN-aware access point (AP). These APs separate incoming wired traffic using the subnet address associated with each VLAN. End nodes receive only the data on the configured subnet.
Security over the air cannot be enforced as it can on a wire. Service set identifiers, or SSIDs, with different passwords are used where necessary, such as in guest networks.
VLANs were developed early in the evolution of networking technology to limit broadcasts and prioritize traffic. They have proven to be useful as networks have increased in size and complexity.






