
James Thew - Fotolia
This PowerShell module takes control of NTFS permissions
One simple install of the File System Security PowerShell Module can help manage NTFS permissions for user access to folders.
Although PowerShell includes a set of native cmdlets for configuring storage, the ability to configure NTFS permissions is noticeably absent. Fortunately, Microsoft does provide a way to retrieve and configure NTFS permissions through PowerShell, but to do so you will need to download and install a dedicated module.
The required module is the File System Security PowerShell Module. Copy the files into a folder named NTFSSecurity within the PowerShell modules folder (you will have to create the NTFSSecurity folder). By default the PowerShell Modules folder is located at: %Windir%\System32\WindowsPowerShell\v1.0\Modules.
Once the module has been copied to the appropriate folder, it is a good idea to verify the module's availability by using the following command:
Get-Module –ListAvailable
Assuming that the NTFS module is listed, you should be able to import it by using the following command:
Import-Module NTFSSecurity
Keep in mind that unless you have changed the server's execution policy via the Set-ExecutionPolicy cmdlet, this command will produce an error message telling you that running scripts is disabled on the system.
Once the execution policy has been imported you will be able to work with NTFS permissions. However, you will have to import the NTFSSecurity module each time that you need to use it.
Say I have created a folder on my server called C:\Data. With that said, let's pretend that we wanted to view the Access Control List entries for this folder. To do so, we could use the following command:
Get-NTFSAccess –Path C:\Data
This command lists each account / security group that has access to the folder, the access rights, what the rights apply to, the type of rights, and the IsInherited and InheritedFrom flags (Figure 1).

You can view NTFS permissions through PowerShell.
Granting access to a folder is almost as easy as viewing the existing permissions. For this task you will need to use the Add-NTFSAccess cmdlet. You will also have to specify the path, the account and the access rights. To see how this works, let's grant "Everyone" full access to the C:\Data folder. To do so, we would use the following command:
Add-NTFSAccess –Path C:\Data –Account Everyone –AccessRights FullControl
Now, I have added a permission that gives Everyone full control over C:\Data and used the Get-NTFSAccess cmdlet to verify the permission (Figure 2).

The Everyone group has been granted access to the C:\Data folder.
Even though I was able to grant permission to Everyone, you normally have to specify an account location (Figure 2). For example some of the existing permissions use locations such as BUILTIN or NT AUTHORITY. In the real world, you usually specify a domain name in conjunction with a group name or a user name. For example, if you wanted to grant access to the Finance group within the Contoso domain then you would enter the account as Contoso\Finance.
Removing NTFS permissions can be a little bit tricky. The command that you must use is Remove-NTFSAccess. As was the case before, you must specify the path, the account name and the rights that you want to remove. For instance, if you wanted to remove the FullControl permission from Everyone for C:\Data, you could use the following command:
Remove-NTFSAccess –Path C:\Data –Account Everyone –AccessRights FullControl
The reason why this command can be tricky is because you cannot remove inherited permissions. Furthermore, the permissions that you remove must be an exact match for the permissions that are currently assigned to the account. If you specify different permissions then nothing will happen.
Because it can sometimes be tricky to match the permissions perfectly, it may be easier to pipe several commands together as a way of removing the permissions. Suppose for instance that you wanted to remove all of the permissions for Everyone from the C:\Data folder. Rather than manually specifying the permissions, you could have PowerShell read and then remove the permissions. The code required for doing so is:
Get-NTFSAccess –Path C:\Data –Account Everyone –ExcludeInherited | Remove-NTFSAccess
It is also possible to use this command recursively if you need to remove permissions from an entire folder tree (Figure 3).
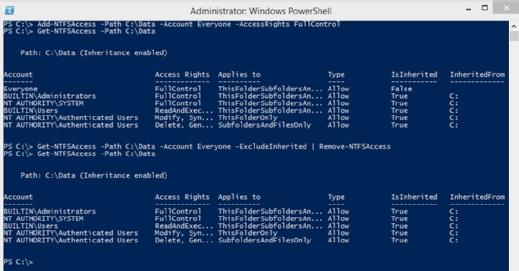
The permissions for Everyone have been removed.








