8 WSUS alternatives for patch management
Compare the features of eight prominent patch management tools for Microsoft OSes and third-party applications to find the right option for your organization.
IT pros commonly use Microsoft Configuration Manager or Windows Server Update Services to manage patches on Windows Server and desktop systems. Both options are well known, widely deployed and integrated into the larger Windows ecosystem, making either one a natural fit for organizations running Microsoft's OSes.
The patch management features in Configuration Manager, formerly System Center Configuration Manager, which is now part of the Microsoft Intune family of products, can help administrators manage the complex tasks of tracking and applying updates. Configuration Manager includes a set of integrated tools for updating software manually or automatically, as well as controlling when and how patches are deployed. It offers other management functions, giving IT a single tool to carry out many of the tasks associated with administering Windows computers.
Configuration Manager uses Windows Server Update Services (WSUS) to synchronize updates and to conduct update applicability scans. However, organizations don't need Configuration Manager to use WSUS, which is a free server role in Windows Server used to manage and distribute updates. Like Configuration Manager, WSUS provides an integrated tool to patch Windows machines but without the expense or overhead.
Why consider WSUS or Configuration Manager alternatives?
Although many organizations use Configuration Manager and WSUS for Windows patching, both products have limitations. For example, some IT professionals consider Configuration Manager to be expensive and overly complex. The product also offers limited support for non-Windows platforms and applications and must be installed on Windows Server.
Like Configuration Manager, WSUS also has to be installed on Windows Server, which can bring additional licensing fees. The product also has a reputation for being inefficient, cumbersome and buggy at times. In addition, WSUS provides only rudimentary automation and little in the way of reporting capabilities.
Third-party patching tools seek to address these limitations, either by extending WSUS or Configuration Manager or by providing a separate tool for patch management. Third-party tools can help streamline and simplify patching operations, while providing greater control over the patching process. But not all patching tools are the same.
Top WSUS alternatives for patch management
Here, in alphabetical order, is a quick summary of eight prominent WSUS alternatives that each take a different approach to updating the Windows OS and the applications that run on it. Read on for details about all eight products.
1. Automox
Automox, a cloud-based, cross-platform system management tool for patch management, software distribution, reporting and policy enforcement, is not purely a patch management tool, but rather an IT operations system. In addition to its patch management capabilities, Automox can be used for configuration management, software deployment and policy enforcement. Another key feature is single-click remediation of vulnerabilities that have been identified by CrowdStrike, Rapid7 or Tenable.
Automox performs patch management of OSes and applications across a variety of endpoints. Agents are currently available for Windows, macOS and Linux, and Automox can natively patch dozens of third-party applications across the platforms.
Automox is a SaaS product, and the vendor offers two types of subscriptions: Standard and Pro. The Standard plan is geared toward organizations that need patch management capabilities. Besides OS and application patching, it includes features such as full device inventories, basic reporting and end-user notifications. Pro includes all the same features as Standard but adds multizone management, automated vulnerability remediation, remote control and other capabilities.
2. GFI LanGuard
Emphasizing cross-platform patch management and vulnerability scanning for smaller organizations, GFI LanGuard is a network security tool for patch management, network auditing and vulnerability detection. It can be used with or without agents, and its reporting engine has been specifically designed to assist with regulatory compliance for HIPAA, PCI DSS, etc. It recently added generative AI for analytics and automated configuration.
GFI LanGuard supports patch management for Windows, macOS and Linux systems, as well as third-party applications. The software scans managed nodes and identifies missing patches but also checks for over 60,000 known vulnerabilities. If a vulnerability is detected, the software provides a graphical indication of the vulnerability's severity, as well as a recommended course of action. GFI LanGuard is also designed to integrate with over 4,000 security applications. Incidentally, GFI LanGuard's vulnerability scanning is not limited to Windows, macOS and Linux. It also supports Apple iOS and Android and can scan some network hardware, such as printers and switches.
GFI LanGuard is licensed based on the number of nodes to be managed. GFI offers three different licensing plans. Each plan is based on an annual subscription and includes all the same features. The only difference between the plans is the cost, with larger organizations paying less per node. GFI LanGuard is also part of the GFI Unlimited plan, which includes licenses for a number of other GFI products.
3. Ivanti Security Controls
An enterprise-grade tool running on physical or virtual hardware, Ivanti Security Controls, formerly Patch for Windows, is a versatile patch management product for Windows computers, VMs and VM templates. It also supports VMware ESXi hosts, Windows applications and Linux distributions, including Red Hat Enterprise Linux and CentOS. Security Controls has a centralized interface designed to make it easy to scan physical and virtual systems, assess and deploy patches, and schedule remote operations while providing granular privilege management to balance access and security.
Admins can configure Security Controls to automatically run scheduled recurring scans and deploy any missing patches that are detected during the scans. Security Controls can detect and categorize software and hardware, track asset inventory over time and control a computer's power state, such as shutdowns and restarts. It also gives admins a way to run PowerShell scripts to carry out tasks or automate operations. The REST APIs integrate Security Controls with other products and support remote access and control while offering a method to automate operations.
Security Controls generates multiple reports that provide a variety of information, such as the installed OSes, machine power states, patch deployments and status, and machine compliance. Admins can use database queries to generate custom reports. Security Controls can display applications and their services and components, as well as import the CVE list. It can also show which patches are related to each CVE.
4. Kaseya VSA
Cloud-based Kaseya VSA is a remote monitoring and management service that includes patch management capabilities to install, deploy and update software on Windows, macOS and Linux machines. It uses policy-based patch management that automates and standardizes software maintenance. Admins can approve, schedule and install patches, as well as schedule regular network scans for analyzing computers and automating software updates.
Kaseya VSA has a centralized console to assist with patch management operations, including uninstalling and repairing software. Admins can scan computers for missing patches, view a summary of the patch status for each machine and exclude patches from specific machines. Kaseya VSA can also run procedures before or after updates. For example, an admin can use a procedure to automate setting up a newly added computer.
Kaseya VSA gives administrators both manual and automated options for updating software while offering granular control over the patching process. Admins can also set up patch reports to see compliance across their environments and quickly identify endpoints and applications that need attention. In addition, Kaseya VSA aggregates the patch status of all machines to see which CVEs need to be addressed on each. Admins can also use the product to access recent network scans to identify installed and missing patches.
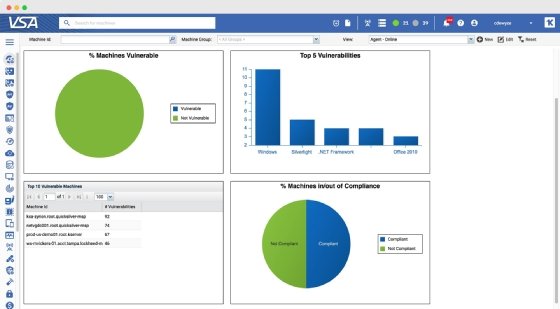
5. ManageEngine Patch Manager Plus
ManageEngine, a division of Zoho, offers Patch Manager Plus, a versatile patch management tool available as on-premises software or as a cloud service. It supports Windows, macOS and Linux endpoints, along with more than 850 third-party applications. Admins can carry out patching operations from a single interface and use the vendor's prebuilt packages to streamline the process. They can also automate patch deployment for OSes and applications.
Patch Manager Plus includes numerous auditing, analytics and reporting features for visibility into the patch status of computers and applications. ManageEngine offers a free edition and two paid editions, Professional and Enterprise. The Enterprise edition is suitable for WAN use, while Professional is designed for LANs. The Enterprise edition includes all of the features found in the Professional edition but adds antivirus definition updates and the ability to test and approve patches. The Enterprise edition also includes a distribution server, which can help conserve bandwidth. The free edition supports similar features as the paid editions but is limited to 20 workstations and five servers.
With the Enterprise edition, IT can automate the entire patch management process. This includes scanning endpoints for missing patches, downloading patches from vendor websites, deploying the patches and generating reports on the patch management process. However, all three editions include such features as service pack deployments, Active Directory authentication, roaming user patching, role-based administration and on-demand remote shutdown.
6. PDQ Deploy
PDQ Deploy from PDQ.com is a lightweight software deployment tool for automating patch management on Windows Server and desktop machines. It supports more than 250 Windows applications, which can be updated using the vendor's prebuilt, pretested packages. In addition, IT can create custom packages, as well as copy over files, send messages to users or force reboots on managed systems. PDQ offers plans for small business, education and enterprise use. Licensing costs are based on the number of admins who will be using the software. A 14-day trial is available.
PDQ Deploy uses a centralized console for installing, uninstalling, updating, repairing and making other changes across the network. The console also provides access to the prebuilt application packages. In addition, PDQ offers a CLI for working with packages.
Admins can also use scripts to automate operations with support for several scripting languages, including Visual Basic, PowerShell and batch files. In addition, IT can set up multiple distribution points for sharing custom packages, schedules and target lists.
For most deployments, admins use the scheduling capabilities to deploy packages at specified intervals. They can also create automatic deployments for new package versions as they become available from the package library. In addition, PDQ Deploy can send an email with details about patch deployments, including which computers or software were updated and which systems might need more attention. Admins can also access built-in reports that provide deployment and scheduling information.

7. Quest KACE Systems Management Appliance
Quest KACE Systems Management Appliance is designed to be a unified endpoint management system that can do far more than just basic patch management. You can also use it for tasks such as software distribution, software license tracking, and server management and monitoring. There is even a mobile app for managing service tickets on the go.
The appliance can perform patch management for Windows, Linux and macOS systems, along with a vast number of applications. Quest uses a system of smart labels that enable admins to classify both endpoints and updates and then perform actions or create reports based on the labels. For example, patches might be labeled by vendor, date or severity. The appliance can also perform automated vulnerability scans, as well as configuration management and policy enforcement. In multisite environments, the appliance can use replication servers to minimize bandwidth consumption during patch management.
Quest offers several deployment options for KACE Systems Management Appliance. It can be deployed as an on-premises virtual appliance or hosted in VMware, Hyper-V, Nutanix or the Microsoft Azure cloud.
8. SolarWinds Patch Manager
Intended for organizations that are already using WSUS or Configuration Manager, SolarWinds Patch Manager offers broad support for third-party applications and more comprehensive reporting capabilities than most tools. It builds on and extends WSUS and Configuration Manager to provide a patch management tool for addressing software vulnerabilities and managing third-party applications. IT teams can automatically apply Windows updates using customized schedules that target specific business groups or system categories, based on such factors as OS or IP range. Patch Manager also helps teams proactively identify which Windows machines need to be patched and then quickly deploy the patches to those systems, including virtualized workloads.
Admins can create pre- and post-update package scenarios to verify third-party patch deployments. Patch Manager includes Custom Package Wizard for admins to build packages for any application without the need for complex scripting or System Center Updates Publisher. SolarWinds also offers prebuilt, pretested application packages that admins can quickly deploy through WSUS or Configuration Manager.
Patch Manager features a web console for centralizing patch management and viewing important patch information. The console offers several reporting options for determining patch status and demonstrating patch compliance to auditors. Admins can also view information about the latest available patches, missing patches on their systems and the general health of the patch environment. In addition, Patch Manager can notify admins when updates become available, either through the console or by email.
Brien Posey is a 15-time Microsoft MVP with two decades of IT experience. He has served as a lead network engineer for the U.S. Department of Defense and as a network administrator for some of the largest insurance companies in America.
Robert Sheldon is a technical consultant and freelance technology writer. He has written numerous books, articles and training materials related to Windows, databases, business intelligence and other areas of technology.







