
icetray - Fotolia
Windows zero-day shut down on November Patch Tuesday
In addition to fixing the exploited Windows flaw, Microsoft rolls out a new look to the Security Update Guide that draws some criticism.
As part of its November Patch Tuesday releases, Microsoft corrected a Windows zero-day vulnerability disclosed last month by Google researchers, who uncovered a coordinated attack method that also affected the Chrome web browser.
Microsoft addressed 112 unique vulnerabilities with 17 rated critical this month. Software with security updates this month include the client and server Windows OSes, Microsoft Office and Office Services and Web Apps, Internet Explorer, both the HTML-based and Chromium-based Microsoft Edge browsers, the ChakraCore JavaScript engine, Microsoft Exchange Server, Microsoft Dynamics, Microsoft Windows Codecs Library, Azure Sphere, Windows Defender, Microsoft Teams, Azure SDK, Azure DevOps Server and Visual Studio.
Windows zero-day tops list of bug fixes
Google Project Zero's security analysts discovered attackers were exploiting an elevation of privilege vulnerability in the Windows kernel (CVE-2020-17087) -- rated important -- and using it in tandem with a Chrome vulnerability (CVE-2020-15999) -- corrected by Google on Oct. 20 -- to exploit Windows systems. This method is commonly called vulnerability chaining in the security field. This combination attack allows the threat actors to escape out of the Google Chrome browser's sandbox to launch malware attacks on Windows systems.
 Chris Goettl
Chris Goettl
"The guidance here is to get this pair -- both Google Chrome and the Windows OS -- patched in a reasonable time frame to plug what you already know is being exploited," said Chris Goettl, senior director of product management for security products at Ivanti, a security and IT management vendor based in South Jordan, Utah.
Researchers from Google's Project Zero disclosed the Windows zero-day after giving Microsoft seven days to correct the bug. The vulnerability affects all supported server and desktop Windows OSes and those in the Extended Security Updates program, specifically Windows 7, Windows 8.1 and Windows Server 2008 and Windows Server 2008 R2.
The Project Zero team follows a seven-day disclosure policy when it finds active exploits of vulnerabilities to spur vendors to produce a patch more quickly. The team released information on the kernel bug on Oct. 29.
Windows Network File System bug could open up wormlike issues
A critical Windows Network File System remote code execution vulnerability (CVE-2020-17051) has the highest severity level for this month's security updates, with a base score of 9.8 out of 10 on the Common Vulnerability Scoring System (CVSS). This bug affects all supported versions of Windows.
According to a blog from McAfee Labs, "CVE-2020-17051 would give adversaries the ability to spread worm-like within heterogenous Windows and Unix/Linux environments using anonymous write access file shares over NFSv3."
Attackers do not require a user on the system to interact with the exploit for it to trigger, Microsoft's CVE said. If patching is not possible, the McAfee blog suggests administrators should restrict write access to server shares in the organization and stop external access to these unpatched servers.
Multiple patches arrive for developer-based products
Administrators in developer-based environments who manage users working with tools such as Visual Studio, Azure DevOps Server or Azure Sphere should note there are multiple fixes for those products this month. For Azure Sphere, Microsoft's operating system designed for use with the company's internet of things (IoT) platform, there are 15 unique vulnerabilities, including one rated critical (CVE-2020-16988).
"If you're running an Azure IoT device and it's connected, it should get updated daily, which you can check by running a couple of commands," Goettl said.
The Azure Sphere program reached general availability in February and had not gotten any security updates until this month.
"The Azure Sphere and [Microsoft Security Response Center] bounty team completed a three-month security research challenge, in which we invited researchers to find and report vulnerabilities in the Azure Sphere OS," Microsoft wrote in the CVE FAQ.
Azure Sphere has an automatic update system, but Goettl said administrators should check that the patches were successfully deployed due to the large number of fixes Microsoft rolled out.
Other security updates of note for November Patch Tuesday
- Administrators who manage on-premises Exchange Server systems have three CVEs (CVE-2020-17083, CVE-2020-17084, CVE-2020-17085) to deploy this month with the remote code execution vulnerability (CVE-2020-17084) having the highest CVSS score.
- SharePoint continues to draw interest from attackers with six CVEs addressed on November Patch Tuesday. Most of the vulnerabilities (CVE-2020-16979, CVE-2020-17015, CVE-2020-17016, CVE-2020-17017, CVE-2020-17060 and CVE-2020-17061) have a rating of important.
Microsoft revises Security Update Guide
November Patch Tuesday ushered in an update to the database-style layout for the Security Update Guide, the website that details the vulnerabilities in Microsoft's software with additional details to mitigate a vulnerability if a complete fix is not available.
The database format debuted in February 2017 after Microsoft shed the more verbose bulletin-style presentation that had limited filtering capabilities. The company said it made the switch in part to give administrators a way to tailor vulnerability information specific to their needs, such as displaying just critical Windows Server updates instead of every CVE for a particular Patch Tuesday.
Some key information in the new version continues to evade administrators who have not developed a way to scrape information from the database using the Security Update API. For example, there is no way to list just the vulnerabilities that have been exploited or publicly disclosed. Finding this information requires either checking each CVE manually or using PowerShell and the site API to produce a more granular report.
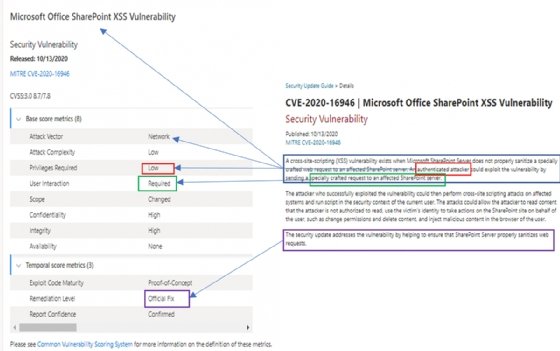
It appears Microsoft also removed the description that typically tops the CVE listing. These overviews would give descriptions of possible attack scenarios on the affected technologies. For example, some of the overviews would indicate if the attack involved a specially crafted file, or if the exploit would launch from Microsoft Outlook's preview pane or from visiting a website.
Not having this information puts IT workers on the operations side at a disadvantage by not sharing the attack vector or other specific ways the attacker can spring the exploit, Goettl said. Advanced threat actors will have the tools and the expertise to compare changes in the code base to develop an exploit, he said.
"The essential information is already out there, and not having this description is just leaving those who don't have the skill set blind to what the real risks are," Goettl said.
A Microsoft blog that went into more depth about the changes to the Security Update Guide also reported PowerShell scripts used to retrieve data and build Patch Tuesday reports had been updated on the GitHub repository.


