
everythingpossible - Fotolia
How to locate privileged accounts in Active Directory
IT administrators must be able to identify privileged accounts in Active Directory for a more secure enterprise; two methods can make the task easier.
Imagine your organization's compliance officer sends you a high-priority email message asking you to enumerate all high-privileged identities in your Active Directory Domain Services domain. As usual, your due date to complete the task was yesterday.
To get started, you must understand the types of privileged accounts to look for and the tools available to search the domain for each account.
Learn the basics of privileged accounts
In an Active Directory domain, a privileged account is any security principal with elevated rights or permissions. User accounts can map to individual and service account identities where line-of-business applications run.
Active Directory populates the local Administrators group -- which contains every member server or client device -- with the Domain Admins group. Securing the Domain Admins membership is crucial to maintaining an effective security posture.
The most powerful group in an Active Directory forest is the Enterprise Admins universal group followed by Schema Admins, which has the ability to modify the underlying attributes of any Active Directory object. Active Directory includes several subadministrative groups that are created as a result of installing particular server roles, including account operators, backup operators, Dynamic Host Configuration Protocol administrators and domain name system admins.
Look for direct assignments of a domain user account inside a high-privileged group, nested group memberships and key user rights assignments. For example, if the user Joe is a member of the low-privileged manager-staff global group, but the manager-staff group was placed inside a high-privileged group, Joe will have greater permissions whether that was intended or not.
Active Directory can grant user rights to ordinary user accounts, such as a service account that is a member of the Domain Admins global group. By virtue of assigning the service account to key Windows services, the operating system adds one or more user rights to the account. To prevent a greater security risk, do not add service account identities to global admins.
To ensure user rights are correct, you must check privileged group memberships, delegated user rights, delegated permissions to Active Directory itself or Group Policy Objects, and the standard shared folder or New Technology File System permissions.
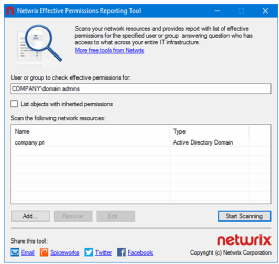
Try the Netwrix tool for user permission reports
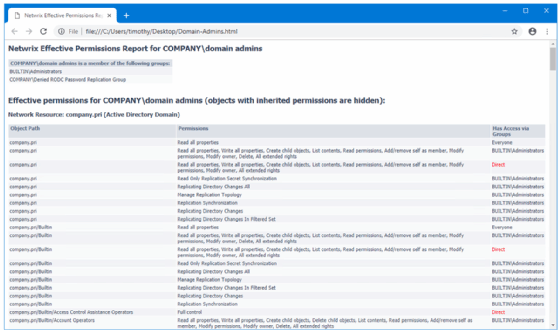
The Netwrix Effective Permissions Reporting Tool can scan your domain and report on effective permissions for a given user or group account. Start the scan by authenticating to Active Directory and focusing on a high-privileged group account.
The Netwrix Effective Permissions Reporting Tool generates a formatted HTML report that shows which groups the target user or group belongs to. The report dives into both directly assigned and inherited permissions across the domain for the chosen identity.
You have to manually re-run the Netwrix tool for every identity, but the tool is free and the reports are basically presentation-ready.
Community scripts can do the work for you
For maximum flexibility in the search to identify high-privileged accounts, turn to Windows PowerShell. In the PowerShell gallery, the AD Account Audit community script from contributor ASabale identifies four account types in your Active Directory domain:
- High-privileged accounts: Users who belong to the Administrators, Domain Admins, Enterprise Admins or Schema Admin groups.
- Limited-privileged accounts: Users who belong to the built-in Server Operators or Backup Operators Active Directory groups.
- System accounts: Built-in identities that Windows uses internally.
- Non-privileged accounts: Ordinary domain user accounts who may belong to a high-privileged group.
The standard rules apply regarding any PowerShell script you download from a community site. Microsoft does vet code placed in the PowerShell Script Gallery. GitHub does not perform quality assurance or security tests on its hosted code. Never run code on a system unless you understand what's going on under the hood. You may need to relax the script execution policy on your system before you can execute scripts.
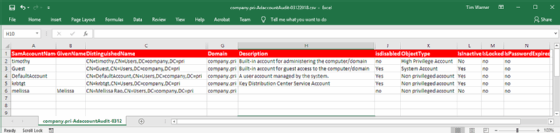
The AD Account Audit script generates a comma-separated value report that lists what privileges those accounts have in your domain. In the figure below, row six of the report shows Melissa, an ordinary user account flagged for elevated privilege. The report prompts an inspection of Melissa's Active Directory user account properties, where you would find that she inadvertently belonged to the Domain Admins global group.
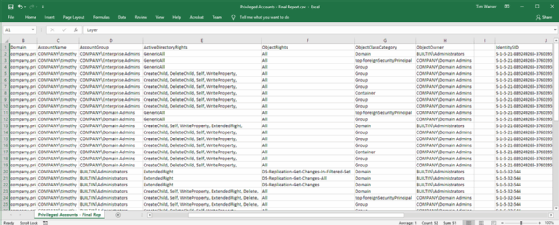
Cyberark's ACLight PowerShell script performs a more comprehensive security scan with the ability to detect shadow admins. Shadow admins are users who do not belong to administrative groups but have elevated privileges through direct assignment of permissions in Active Directory or in the server's file system.
ACLight provides a layers analysis, final report and irregular accounts list. The layers analysis lists privileged accounts and group memberships. The final report gives a detailed permissions list. The irregular accounts list shows accounts that are privileged via access control list permissions, not group membership.
After you identify these security principals, your next task is to conduct an access review to decide which accounts should remain privileged and which accounts you can convert to standard user accounts or decommission.








