
rvlsoft - Fotolia
Using Azure AD conditional access for tighter security
The cloud-based identity and access management service does not come with certain defensive features turned on by default, which administrators should rectify.
As is standard with technologies in the cloud, the features in Azure Active Directory are on the move.
The Azure version of Active Directory differs from its on-premises version in many ways, including its exposure to the internet. There are ways to protect your environment and be safe, but that's not the case by default. Here are two changes you should make to protect your Azure AD environment.
Block legacy authentication
Modern authentication is Microsoft's term for a set of rules and requirements on how systems can communicate and authenticate with Azure AD. This requirement is put in place for several security benefits, but it's also not enforced by default on an Azure AD tenant.
Legacy authentication is used for many types of attacks against Azure AD-based accounts. If you block legacy authentication, then you will block those attacks, but there's a chance you'll prevent users trying to perform legitimate tasks.
This is where Azure AD conditional access can help. Instead of a simple off switch for legacy authentication, you can create one or more policies -- a set of rules -- that dictate what is and isn't allowed under certain scenarios.
You can start by creating an Azure AD conditional access policy that requires modern authentication or it blocks the sign-in attempt. Microsoft recently added a "report only" option to conditional access policies, which is highly recommended to use and leave on a few days after deployment. This will show you the users still using legacy authentication that you need to remediate before you enforce the policy for real. This helps to ensure you don't stop users from doing their jobs.
However, this change will severely limit mobile phone email applications. The only ones officially supported with modern authentication are Outlook for iOS and Android, and Apple iOS Mail.
Implement multifactor authentication
This sounds like an obvious one, but there are many ways to do multifactor authentication (MFA). Your Microsoft licensing is one of the factors that dictates your choices. The good news is that options are available to all licensing tiers -- including the free one -- but the most flexible options come from Azure AD Premium P1 and P2.
With those paid plans, conditional access rules can be a lot nicer than just forcing MFA all the time. For example, you might not require MFA if the user accesses a Microsoft service from an IP address at your office or if the device is Azure AD-joined. You might prefer that both of those scenarios are requirements to avoid MFA while other situations, such as a user seeking access on a PC not owned by the company, will prompt for extra authentication.
MFA doesn't have to just be SMS-based authentication. Microsoft's Authenticator App might take a few more steps for someone to set up the first time they register, but it's much easier to just accept a pop-up on your mobile device as a second factor of authorization, rather than waiting for an SMS, reading the six-digit number, then typing it into your PC.
Without MFA, you're running a high risk of having an internet-exposed authentication system that attackers can easily try leaked credentials or use spray attacks until they hit a successful login with a username and password.
The other common attack is credential phishing. This can be particularly successful when the threat actor uses a compromised account to send out phishing emails to the person's contacts or use fake forms to get the contact's credentials, too. This would be mostly harmless if the victim's account required MFA.
Accounts in Azure AD will lock out after 10 failed attempts without MFA, but only for a minute, then gradually increase the time after further failure attempts. This is a good way to slow down the attackers, and it's also smart enough to only block the attacker and keep your user working away. But the attacker can just move onto the next account and come back to the previous account at a later time, eventually hitting a correct password.
Azure AD conditional access changes are coming
The above recommendations can be enabled by four conditional access baseline policies, which should be visible in all Azure AD tenants (still in preview), but it appears these are being removed in the future.
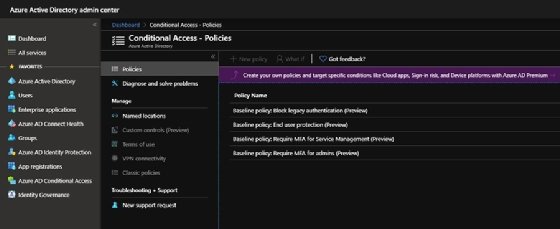
The policies will be replaced by a single option called Security Defaults, found under the Manage > Properties section of Azure AD. The baseline policies helped you be a bit more granular about what security you wanted and the enablement of each feature. To keep that flexibility, you'll need Azure AD Premium once these baseline policies go.
Turning on Security Defaults in your Azure AD tenant will:
- force administrators to use MFA;
- force privileged actions, such as using Azure PowerShell, to use MFA;
- force all users to register for MFA within 14 days; and
- block legacy authentication for all users.
I suspect the uptake wasn't enough, which is why Microsoft is moving to a single toggle option to enable these recommendations. I also hazard to guess that Microsoft will make this option on by default for new tenants in the future, but there's no need for you to wait. If you don't have these options on, you should be working on enabling them as soon as you can.








