Active Directory forest (AD forest)
An Active Directory forest is the highest level of organization within Active Directory. Each forest shares a single database, a single global address list and a security boundary. By default, a user or administrator in one forest cannot access another forest.
AD forests can be used to isolate Active Directory trees with specific data and give autonomy to the user to interact with the data. Several models for AD forests exist, all with advantages and disadvantages depending on organizational needs.
How do you create an AD forest?
The first step in creating a new Active Directory domain forest is to install Windows Server. After doing so, the Active Directory Domain Services role and the DNS Server role needs to be deployed. Once these roles have been installed, the user can promote the server to a domain controller.
When the option to promote a server to a domain controller has been chosen, Windows launches the Active Directory Domain Services Configuration Wizard. This wizard's initial screen provides an option to create a new forest. The user can simply choose this option, specify a root domain name and follow the remaining prompts.
Advantages and disadvantages of AD forests
The primary advantage to creating an Active Directory forest is that the forest acts as a centralized mechanism for managing and controlling authentication and authorization across the organization. Administrators can create user objects (user accounts) within the Active Directory. These user objects act as security principals, meaning that the Active Directory can authenticate logins.
Additionally, group policy settings can be applied at various levels of the Active Directory hierarchy to enforce user account or computer configurations. For example, group policy settings can be used to enforce password length and complexity requirements for user accounts.
Administrators are also able to create security groups within the Active Directory. These security groups act as collections of user objects and play an important role in data security. Security groups are typically linked to the access control lists associated with folders and other resources, thereby granting permissions to group members.
Disadvantages include security vulnerabilities, such as the possibility for more exploitation. While using a multi-forest design could be an option, it is not secure by default because it still requires setup for permissions and authentication for each forest. Multi-forest designs also increase costs. It's recommended to consolidate AD forests as much as possible to reduce cost.
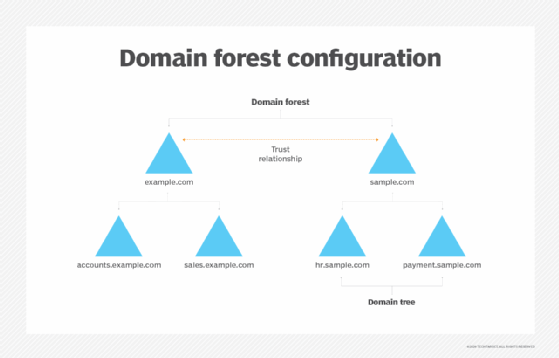
Forest design models
Active Directory forests can be constructed according to several different architectural models, including:
- Organizational forest model
- Resource forest model
- Restricted access forest model
The simplest of these models is the organizational forest model. In smaller organizations, this model establishes a single AD forest that contains all the organization's resources. Larger organizations may have a separate Active Directory forest for each department or division. Creating multiple AD forests provides an isolation boundary between departments. If collaboration is required between departments, a forest level trust can be created.
A second type of forest model is the resource forest model. In this model, user accounts are created within an organizational forest. Separate forests are created to accommodate the resources related to individual departments, divisions or projects. These resource forests do not contain user accounts aside from those required for administrative purposes. Instead, trust relationships allow users from the organizational forest to access resources in resource forests. Resource forests are a good choice for helping to isolate problems. An Active Directory problem occurring in one resource forest will not affect another resource forest because of the forest level boundaries that are in place.
A third forest design model is the restricted access forest model. The This model involves multiple forests, with no trust relationships between them. The users in one forest cannot access any of the resources in another forest. This design is used in high-security environments because it creates extremely strong isolation boundaries.
Single forest vs. multi-forest AD design
Although various forest design models allow for the creation of multiple Active Directory forests, such models are complex and expensive to implement. Typically, only the largest organizations use them.
Smaller organizations that want to have structures that are somewhat similar, but less complex by can create a single forest with multiple child domains. These child domains can be dedicated to a particular department, project, division or resource. Additional domains can be easily created on an as-needed basis to meet the organization's operational and organizational requirements.
Best practices
The Active Directory was designed so that a domain or a forest can contain domain controllers running a variety of Windows Server versions. In a domain, the domain functional level setting determines the oldest Windows Server version that can be used as a domain controller in that domain. Similarly, the forest functional level determines the oldest Windows Server version that can be used on a domain controller within the forest.
Functional levels allow domain controllers running on newer operating systems to be fully backward compatible with older domain controllers. However, this means that some domain controllers that are set to an older functional level do not support newer features until the functional level is raised. For example, a Windows Server 2019 domain controller with a domain functional level of Windows server 2012 will act like a Windows Server 2012 domain controller, and Active Directory features that have been introduced since Windows Server 2012 will not be available. As a best practice, organizations should periodically review their domain controller operating system versions and raise the domain functional levels and forest functional levels accordingly.
There are also best practices surrounding global catalog placement. Global catalogs help with user logon requests and Active Directory searches. In a single domain forest, every domain controller should act as a global catalog server. Typically, this is also the case in multi-domain forests. However, the user might not designate a domain controller as a global catalog server if the domain controller is bandwidth constrained or if it is the domain's infrastructure master (unless all domain controllers are global catalog servers or the forest only has one domain).






